EXECUTIVE SUMMARY
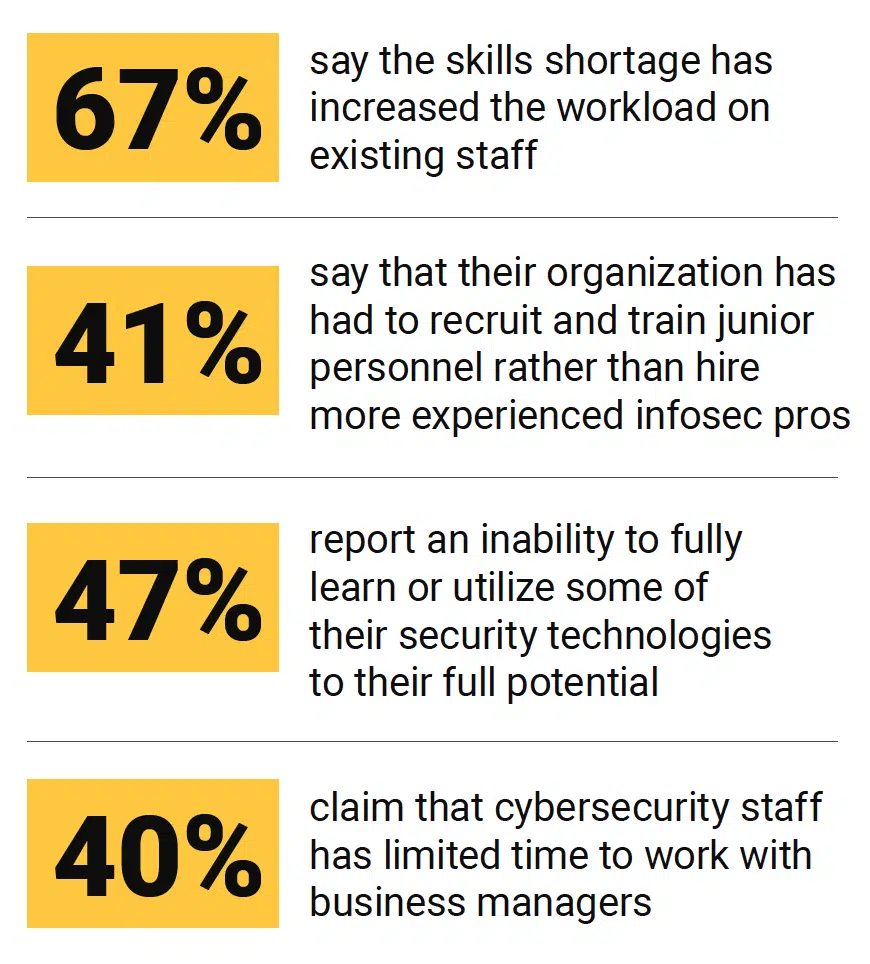
Today’s threat landscape is constantly evolving. Sophisticated cyber threats are becoming smarter and faster, leading to an increase in security breaches and unprecedented fines for non-compliance. Simultaneously, organizations are rushing to drive increased business agility through digital transformation, embracing emerging technologies like mobility, cloud computing, largescale virtualization, software-defined networking, and the hyperconnected Internet of Things. Yet, organizations worldwide face an inability to hire and retain skilled security professionals, putting additional strain on lean security teams and increasing their security risk.
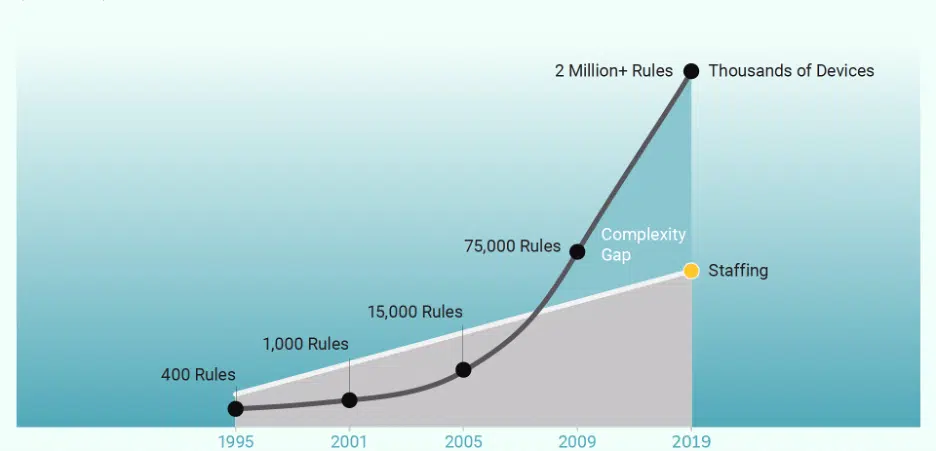
The result is a complexity gap where emerging network and cloud technologies outpace security teams’ ability to secure and manage their expandingenvironments perimeters, severely inhibiting business agility. Organizations find themselves at a crossroads – they must ensure that security doesn’t slow down innovation and that innovation doesn’t compromise security. Closing the complexity gap at scale requires automation of network security functions to replace manual, error-prone processes, maintain regulatory and internal compliance, and reduce overall security risk. This will increase the efficiency and efficacy of security teams, drive business innovation, enable business agility, and improve the bottom line.
This post describes how the complexity gap is impacting organizations and the pivotal role network security policy automation plays in helping organizations reduce risk and enhance their overall security posture.
The Bottom Line
Automation of key network security functions will provide much needed consistency and control across hybrid network environments required to reduce the complexity gap. It will enhance compliance efforts, reduce risk, and improve productivity for time- and resource-strapped security teams. As a result, organizations can improve their overall security posture, meet regulatory and internal compliance requirements, and achieve the business agility they need to keep up with the growing demands of the business.
Sidebar: Fast Facts
- The rapid pace of digital transformation demands error prone, manual network security processes be automated.
- It is increasingly difficult to maintain consistent, continuous compliance of network security devices from multiple vendors and eliminate costly misconfigurations caused by human error.
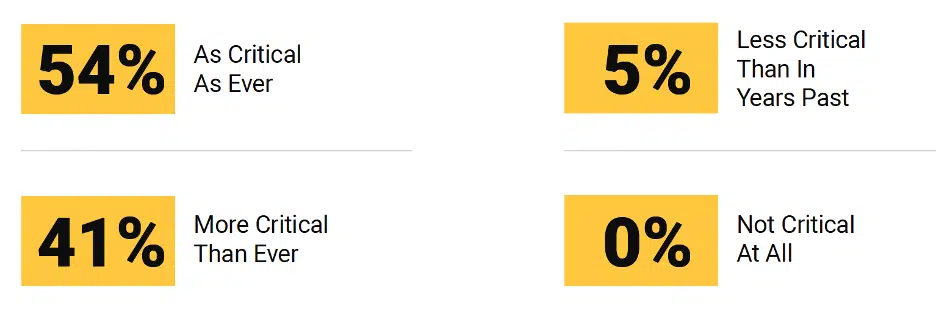
- Security policy enforcement points are not only a vital part of the network security architecture, they are growing in criticality as networks expand in scope and complexity across multiple environments.
- An intelligent network security platform will provide the automation and analysis capabilities needed to tame network sprawl and enable security practitioners to make better-informed decisions based on context and actionable intelligence.
- Centralized management is essential in order to provide real-time visibility and control over the hybrid network and a central policy enforcement point.
- Advanced analytics and security intelligence capabilities will enable better decision making and help detect, prevent, and proactively respond to threats.
Technology Sprawl Adds to Complexity
Hybrid networks have become increasingly complex, both in terms of the number of endpoints and technologies in use. The explosive growth in the number of mobile devices and the emergence of the Internet of Things (IoT) has massively accelerated endpoint proliferation. Cloud-based applications and services have also grown in popularity, driven by the flexibility, speed, and convenience they offer.
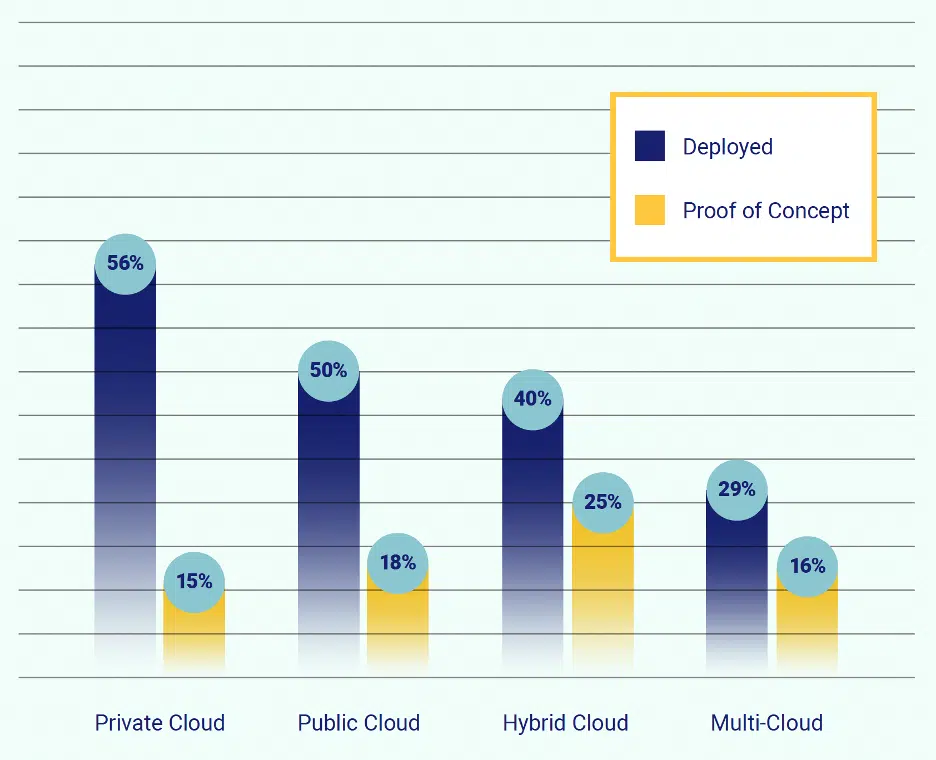
Sidebar: Cloud Adoption Outpacing Security – 60% of respondents say cloud business initiatives are accelerating faster than security teams’ ability to secure them.
Because organizations tend to use multiple security vendors in a hybrid cloud environment, they may be unintentionally, or intentionally, adding to the complexity of managing and securing their networks. The FireMon 2019 State of Hybrid Cloud Security report showed that 59% of respondents use two or more different firewalls in their environment, with 67% of those using two or more firewalls also using two or more public cloud platforms.